Compared with earlier mobile-network technologies, 5G brings a range of security improvements. GSMA, a global industry organization representing mobile network operators and telecom suppliers, refers to 5G as “secure by design.” That description reflects a series of principles applied during the concept, design, and development stages to build security into 5G networks. This security-oriented approach helps make cybersecurity contextual and even predictive—characteristics that help to anticipate and close off potential vulnerabilities.
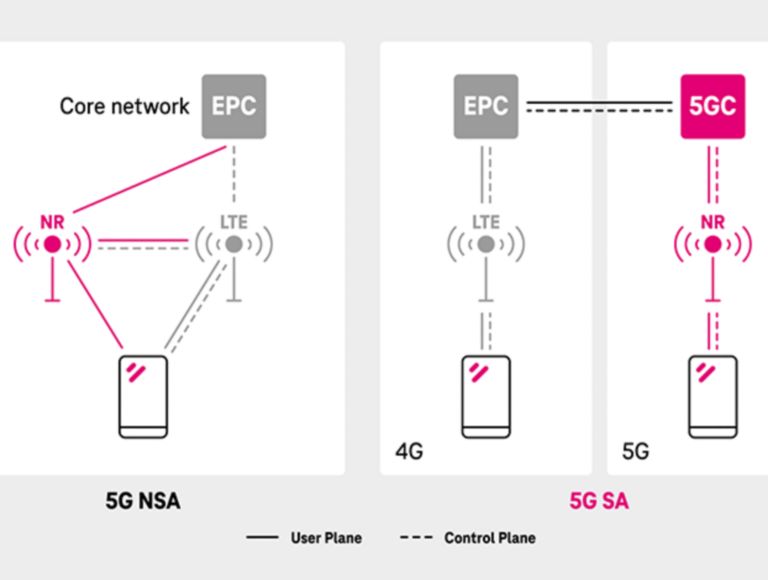
The security advantages are greatest with what’s called 5G Standalone (5G SA), which requires that mobile devices and network infrastructure equipment support 5G specifications. By comparison, 5G Non-Standalone (5G NSA) is overlaid on an existing 4G network, only providing higher bandwidth locally where it’s available.
TWO 5G DEPLOYMENT MODELS
Non-Standalone Access (NSA) and Standalone Access (SA).
- NSA provides more broadband capacity since it acts as a supplementary overlay to 4G.
- SA provides all the features of NR as well as the capabilities of the new core network.
In addition to being used for public or “macro” 5G networks, 5G SA infrastructure can be used to create private 5G networks at manufacturing sites, office campuses, and other business environments with unique and highly demanding connectivity needs.
An entirely different kind of network.
5G’s advances are made possible by the “softwarization” of the mobile network ecosystem, as the network becomes increasingly software defined. This new architecture offers more flexible service configuration and delivery, making it well suited to enterprise applications and networking requirements.
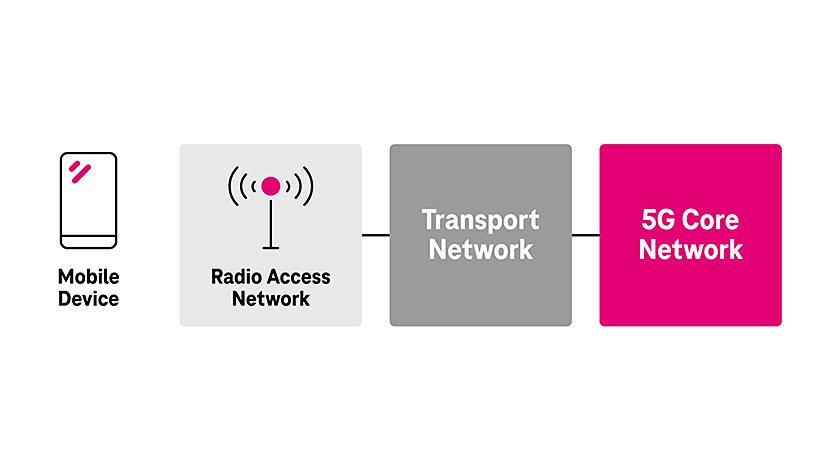
5G SA consists of:
- A Radio Access Network (RAN), which provides wireless connectivity to devices
- A transport network, which establishes connectivity between the RAN and the core network
- A core network, which allows subscribers to get access to services, such as mobility, authentication and authorization, charging, and session management
The core network provides coordination between different parts of the access network, as well as connectivity to the internet and the core networks of other telecom operators.
In the core network, signaling is handled by a Service-Based Architecture, replacing the monolithic approach of the 4G core network. In 5G’s service-oriented model, signaling is processed by interconnected Network Functions—typically virtual instances—each of which must request authorization to access another’s services.
In addition to this modern network architecture, 5G SA incorporates other capabilities that help bolster security. They include:
- Network slicing, where services are rendered on virtualized logical networks running on the same physical network infrastructure.
- Use cases for 5G network slicing range from improved quality of service (QoS) for common applications such as public safety communications and traffic management, to emerging scenarios like industrial automation and connected smart vehicles where network performance is vital to business outcomes and user experiences.
- Each network slice is an isolated end-to-end network, tailored to the requirements of a particular application or customer. Different levels of security can be applied to each of these custom slices by engaging such functions as authentication and access control.
- Network slicing lifecycle management. According to 3GPP, this includes the following phases:
- Preparation covering overall slice design, capacity planning, and onboarding
- Commissioning to ensure that all needed resources are allocated and configured
- Operation including activation of the network slicing instance, performance monitoring/reporting, and deactivation
- Decommissioning where the slice is terminated and resources are no longer allocated
How 5G SA delivers enterprise-class security.
Security has been factored in from the initial design phase of 5G SA. Many known vulnerabilities present in previous cellular networks have been addressed.
Encryption provides added protection throughout 5G SA. It’s used for interfaces, subscriber identities, the network control plane, and the user plane that carries user data traffic. What’s more, 5G SA provides Transport Layer Security encryption and authentication of traffic between network operators.
Even with all of these advances, organizations must stay vigilant about any new risks that might be associated with 5G-enabled use cases. For example, 5G SA allows for more expansive Internet of Things (IoT) networks, which means many more devices must be protected. And as more organizations deploy edge computing, they must ensure that edge servers and nodes are not exposed.
The good news: 5G SA networks are more flexible and adaptive thanks to software-defined networking and virtualization. And telecommunications equipment manufacturers are moving away from “waterfall” development—where software is developed in phases—to Continuous Integration/Continuous Deployment, allowing for faster development of new features and improvements. Also, more telecom manufacturers are adopting container software, yet another way of securing data.
| Known Security Control Gaps | 4G and 5G Non-Standalone | 5G Standalone |
|---|---|---|
| Subscriber privacy – IMSI tracking (Over-the-air location tracking) |
Vulnerable | Mitigated via IMSI ciphering (SUPI/SUCI) |
| Secure signaling UE / Core flows (Non-access stratum messages) |
Vulnerable (uses encapsulation) | Partially mitigated (encryption after key distribution) |
| User plane integrity protection (Prevents over-the-air replay attack and injections) |
Vulnerable (optional feature) | Mitigated starting in Release 16. (mandatory feature but optional for implementation) |
| Secured core network data flows | Vulnerable | Mitigated via SBA and Secure APIs |
| End-to-end customer traffic isolation | Vulnerable | Mitigated via End-to-End Network Slicing (e.g., UE to the Cloud) |
| Downgrade attacks (Force the UE to use earlier 3GPP releases) |
Vulnerable | Mitigated via anti-bidding down between architecture |
| Supply chain security | Vulnerable | In progress (e.g., NESAS / SCAS) |
5G Standalone thwarts “bidding down,” a common tactic among intruders seeking to penetrate wireless networks. #5GHQ
Another noteworthy security improvement: 5G SA thwarts “bidding down,” a common tactic among intruders seeking to penetrate wireless networks. That’s when intruders send malicious commands to trick a network into operating at an earlier cellular standard—such as 3G or even 2G—to avoid the advanced security built into later releases. 5G SA employs Anti-Bidding Down Between Architectures (ABBA) to prevent this practice.
Industry-wide collaboration and implementation.
5G already offers the best performance for a wide range of applications—and it’s evolving to meet new use cases, like IoT devices at scale. With an eye on the path ahead, we at
We’re also a founding member of the 5G Security Industry Test Bed, which brings together wireless carriers, equipment makers, and others to help identify, mitigate, and respond to evolving threats. And we work with industry partners to ensure that all devices and network components have been audited and tested to meet strict security requirements.
Of course, no system is 100 percent secure. Even if the network is impenetrable, the applications that run on top of it or the physical security of corporate data centers still require constant vigilance.
But moving from 4G to 5G SA is a big step forward in creating a more robust security posture, in addition to the many other opportunities offered by faster, more reliable networking. At the end of the day, this translates into more secure networking and operations—and greater confidence in customer privacy.
