Online safety and account protection.
Time to read: 10 minutes
Last updated: October 1, 2024

Time to read: 10 minutes
Last updated: October 1, 2024


Understand the different ways fraudsters try to access your information—including phishing, malware, and account takeover schemes.

Get tips and tools on account protection in your

Stop and think before engaging with anything that seems suspicious—it’s one of the best ways to protect yourself online.
Your phone’s Subscriber Identity Module (SIM) card stores information, like your phone numbers, service details, and, in some cases, text messages. Most phones still use a removable SIM card, but some have a permanent, electronic eSIM chip. There are ways to protect both from scammers.
Enable SIM Protection
SIM Protection is a free feature for
Set a security SIM PIN
If your device is lost or stolen, you can prevent someone else from re-using your SIM by setting a strong PIN code that’s hard to guess—for example, don’t use 1234 or 1111. Visit this tutorial to learn how to set your confidential PIN.
Visit our SIM Protection page for more information.
Never confirm your sensitive personal data or account information in response to an unsolicited email, text, or inbound call.
SMS phishing or SMShing
If you’re a
Email phishing
If you receive a suspicious email, please report it to your email service provider as spam or a phishing attempt.
Voice phishing or vishing
If you’re unsure who’s calling, it’s best to let the call go directly to voicemail. With our free
Learn more in our Help with scams & spam support page.
Port Out Protection, also known as Port Out Protection, is a free feature to safeguard you from unauthorized number ports and potential fraud. It’s currently available to all

You’ve probably heard terms like “identity theft” and “online fraud,” which are shorthand ways to describe when someone attempts to gain access to or misuse a person’s information—like opening new credit accounts or taking over an existing account.
Along with using the tools we offer at
Fraudsters have many ways to try to access your information. They might try to log in to an online account (such as a

Fraudsters send an e-mail or text message or make a phone call to con someone into providing personal information (e.g., email address, passwords, etc.) directly or by visiting a bogus website.

Fraudsters con someone into visiting a website or downloading an app, malware software, or file that appears to be from a legitimate source. Once the malware is on the device, it collects personal data. And when the fraudster demands a ransom payment for the release of that data, it’s then called ransomware.

A technique involving interception of information intended for someone else. This might happen in connection with other techniques. For instance, the interception might occur through malware the fraudster placed on your device, or as a result of a phishing effort that leads you to a fake website that captures information you intended to enter on a legitimate site.

A person poses as someone else to gain access to account information. One common pretexting scheme involves impersonation based on information the fraudster knows about the potential victim.

A fraudster impersonates you and transfers your phone number to a device they control. They do this either by switching your phone number to another carrier or swapping the SIM card assigned to your phone number without your permission.
Customers have legitimate reasons to do both—for example, you may choose to switch carriers or need to replace your SIM card if you lose your phone. But fraudsters try to misuse these functions to gain control of your phone number and gain access to your online accounts (like email and online banking). Read How
Cybersecurity is the practice of protecting systems, networks, programs, and technologies from digital attacks. At
Like any corporation,
That’s why we created the
There are simple steps you can take to help protect yourself online—whether in your T‑Mobile account or other accounts. One of the best ways is to remain vigilant and monitor your online accounts, bank statements, and credit reports regularly for unauthorized activity.
Learn how your online accounts work and manage your security settings. For example, understand how the applications and online platforms you use authenticate your identity and what choices you have for authentication.
There's no way to completely ensure online safety, but here are some considerations:
Use strong passwords with a combination of letters, numbers, and special characters for your T‑Mobile ID and other accounts. Change your passwords periodically and anytime there’s any sign of misuse. Don’t reuse passwords you’ve used for other sites. Don’t give others your passwords or provide them via phone or email.
Reset your T‑Mobile ID password.
Remembering a lot of passwords can be difficult and even risky—that’s where password managers come in. These tools help you generate strong passwords and store them in an encrypted place—all while only having to remember one password to access them. A few password managers we recommend are 1Password, Apple's iCloud Keychain, KeePass, and LastPass.
Keep your home computers and mobile devices safe by running regular software updates and security patches. Consider changing your software update option to "Auto Update" for all software on your computers and mobile devices.
Apply two types of identification on accounts where you can, including on your T‑Mobile.com account. For other accounts, review the security options offered by the account provider.
Add two-step verification to your T‑Mobile.com account.
Have your notifications turned on for logins from other devices on all the accounts you use. Getting notified of suspicious behavior right away is one of the best ways to get ahead of fraud. You can turn on notifications in the settings of the accounts you use, including your
Biometric data is electronic information about your physical or biological characteristics—like a face or fingerprint scan—that is used to identify you. We recommend enabling Face ID, Touch ID, or Fingerprint ID on your devices. It’s actually safer than a password because it’s unique to you and can’t be misplaced or forgotten.
Scans of your face and fingerprints are not stored on your personal device in the same way that a photo might be. Instead, your biometric data is converted into a unique mathematical representation that can’t be stolen, shared, or copied.
At
To learn more about biometric data, read our Cookies and tracking article.
It’s easy to set up this feature by following the steps at the links below. Once you’ve enrolled, you can quickly and securely unlock your phone, sign in to apps and accounts, and even authenticate purchases.
How to set up Face or Fingerprint ID on an Android device.
Your phone’s Subscriber Identity Module (SIM) card stores information, like your phone numbers, service details, and, in some cases, text messages. Most phones still use a removable SIM card, but some have a permanent, electronic eSIM chip. There are ways to protect both from scammers.
Set a security PIN
If your device is lost or stolen, you can prevent someone else from re-using your SIM by setting a strong PIN code that’s hard to guess—for example, don’t use 1234 or 1111. Visit this tutorial to learn how to set your confidential PIN.
Enable SIM Protection
We make it easy and free to lock your SIM card so changes can’t be made to your phone without your permission. To activate your SIM Protection, log in to your
Visit our SIM Protection page for more information.
If your
Get lost or stolen device help.
For
It’s also a good idea to review the details of your wireless service plan to see if you have a benefit called “Lost or stolen protection.”
Never confirm your sensitive personal data or account information in response to an unsolicited email, text, or inbound call.
SMS phishing or SMShing
If you’re a
Email phishing
If you receive a suspicious email, please report it to your email service provider as spam or a phishing attempt.
Voice phishing or vishing
If you’re unsure who’s calling, it’s best to let the call go directly to voicemail. With our free
Learn more in our Help with scams, spam, and fraud support page.
Use anti-malware software from a trusted source and always keep it up to date by letting the software update its file of known issues, called signatures.
For
It’s also a good idea to review the details of your wireless service plan to see if your benefits include McAfee® Security. It can help you stay safer online by protecting your identity and privacy.
Protect yourself by not clicking links or opening attachments from unknown senders. Suspicious links can contain malware or ransomware—a type of malware that encrypts or locks your computer files and demands payment to a fraudster to get them unlocked. Stop and think before you click on something from an unknown or suspicious sender.
Be cautious when using public
If you’re using your smartphone, tablet, or PC as an access point for other devices to connect to the internet, always enable
At home, consider encrypting your home network by updating your router settings to either WPA3 or WPA2 Personal.
The national Do Not Call registry gives you the choice about whether you receive telemarketing calls. Once your number is on the registry, commercial telemarketers are not allowed to call you. Other types of organizations may still call you, like charities, political groups, and debt collectors.
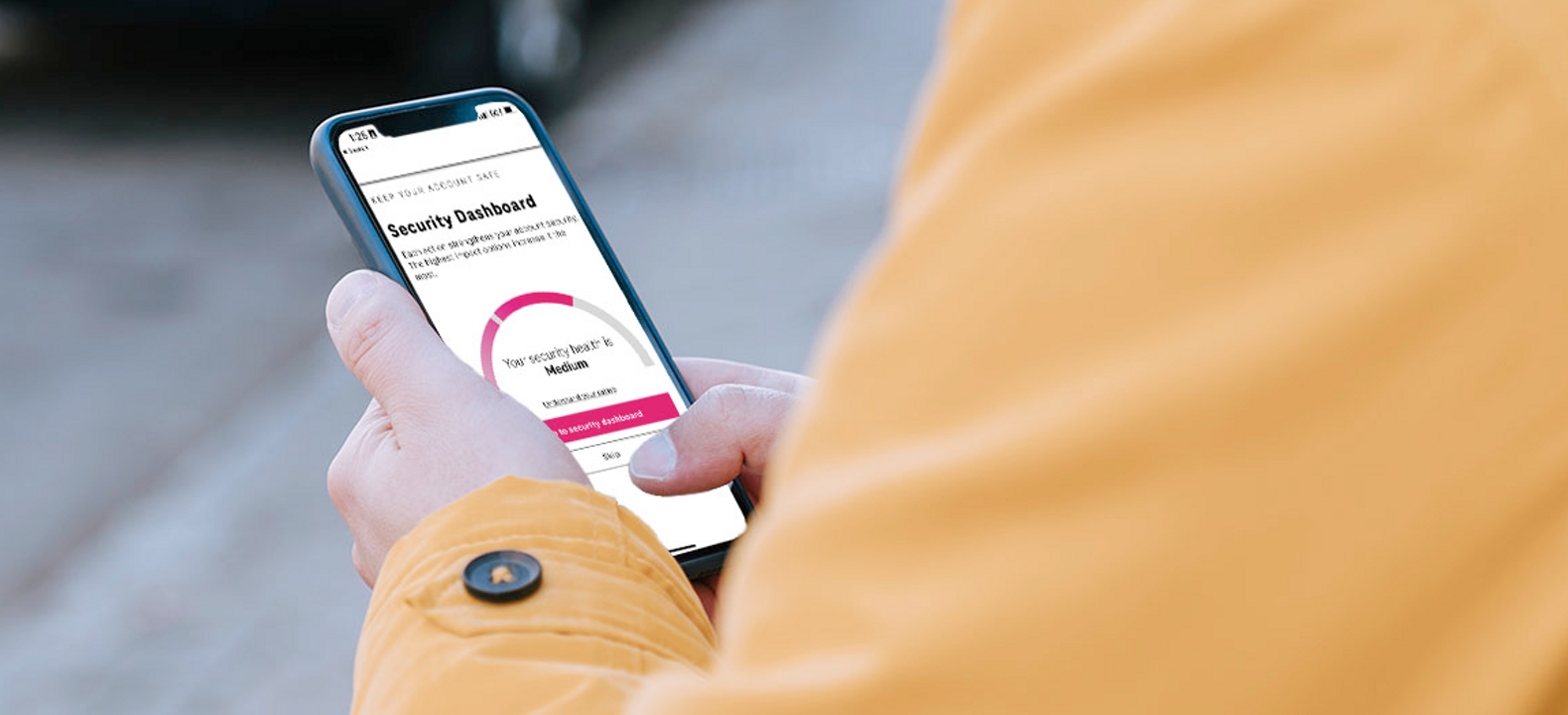
We also offer additional ways to protect yourself and keep your personal data secure. Safety tools provided by
Take simple steps to better secure your
Port Out Protection, a free feature for T‑Mobile Postpaid and T‑Mobile for Business customers, adds protection steps before your phone number can be ported to another carrier.
Prevention is key in protecting yourself from scams.
PROXY gives you an extra number to use when you don’t want to share your private phone number. Calls, voicemails, and texts are accessible any time in the DIGITS app.
You can change your phone number—for any reason—up to one time per year at no extra charge.
If you believe you’ve been impacted by any form of online fraud—including an identity theft incident or a breach of your personal information—you should:
Call your account providers, including your financial institutions and wireless provider, change your passwords, and take additional steps they may recommend.
File a report with the FTC.
File a police report with your local authorities.
Check with your state Attorney General for resources particular to your state.
Contact one of the three credit bureaus—Equifax, Experian, or TransUnion. Whichever bureau you alert will notify the other bureaus of your fraud alert. Also consider placing a credit freeze—which requires you to contact all three bureaus separately—or a credit lock. Both prevent others from taking out credit in your name without your knowledge.
Report directly to the companies where you believe fraud has occurred. To report unauthorized T‑Mobile activity, immediately contact Customer Care by dialing 611 from your T‑Mobile phone or 1-800-937-8997 from any other device.
T‑Mobile will fully cooperate with any investigation undertaken by law enforcement. For legal document requests, please forward a subpoena or court order to: T‑Mobile Law Enforcement Relations Group, 4 Sylvan Way, Parsippany, NJ 07054. Fax: 973-292-8697
Under the Fair and Accurate Credit Transactions Act (FACTA), you have a right to access and receive information related to suspected identity theft. To obtain this information from T‑Mobile, you must send us the following items:
Most frequent requests include copies of bills, credit applications, or shipping requests. Please note, copies of video surveillance require a legal document request. Please mail or fax a copy of each of these to the following address or fax number:
T‑Mobile
Attn: Fraud Management/FACT
PO Box 90880
Allentown, PA 18109
Fax: 813-353-6262
There’s a lot of great information available from government agencies and others about identity theft protection and online safety. We recommend:

Learn how we handle data use and collection for children. And how you can control your kids’ data with a

Take control of your privacy on websites outside of

How you can access, delete, or correct the personal data we have about you.